Demystifying the Security Implications in IoT Device Rental Services
Weakness in Teld charger's authentication
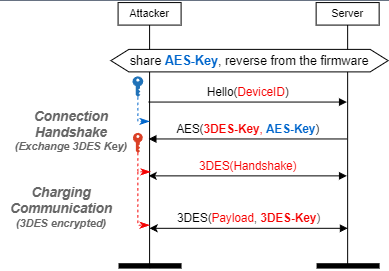
The customize protocol may contain complex message sequences for handshake and key exchange. The Teld charger uses a hardcoded AES key for the initial phase of communication, and they exchange a new 3DES key over the AES encrypted channel, which is used for encrypting the following packets. We identify different message formats by clustering the message traces and implementing them in the phantom clients. During implementation, we use the existing message traces to test the correctness of our Python decode and encode functions. Finally, we feed the necessary parameters to the phantom clients, including the server IP and port, encryption keys, and device identifiers, which are all extracted from the firmware.
Attacking the payment of companion apps
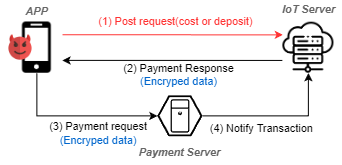
The client (i.e., app) starts a new transaction by sending a device usage request to the server, which may contain detailed information about the selected device such as the device serial number. The server returns a payment request to WeChat and users can pay via the WeChat Pay Service.
Forge multiple states of a local/remote device
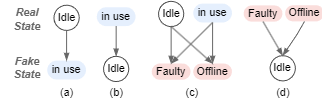
Attackers can forge multiple states of a local/remote device to cheat the server: (a) change an idle device to an in-use state can hinder other users from finding free devices on apps; (b) change an in-use device to idle can cheat other users into checking this unusable device; (c) change an idle or in-use device to faulty can cheat both users and maintainers; (d) change a faulty or offline device to idle can hinder the maintainers from repairing it.
Application Vulnerabilities
| Vendor | Vulnerability Details | Impact | ID | |
|---|---|---|---|---|
| A1 | LuLuChong | 5 APIs leak user’s profile and order infomation | Privacy leakage | CVE-2024-32395 |
| A2 | LuLuChong | The device stop API does not verify user access. | Device manipulation | |
| A3 | QSXM | Forge payment argument to alter price | Use device in free | CNNVD-2023-76976427 |
| A4 | HQJL | Forge payment argument to alter price | Use device in free | CNNVD-2023-24008724 |
| A5 | Dadaball | Forge payment argument to alter deposit amount | Use device in free | CNNVD-2023-76957151 |
| A6 | QiXin | Forge payment argument to alter price | Use device in free | |
| A7 | QiXin | Leak device ID in map API | Device enumeration attack | |
| A8 | Teld | A sensitive setting API does not verify user access | Hijack administrator permission to use device in free | |
| A9 | Teld | Leak device ID in map API | Device enumeration attack | CVE-2024-28307 |
| A10 | Protivo | One API can login to other user's account using the phone number | Account hijack | |
| A11 | Protivo | Leak device ID in map API | Device enumeration attack | |
| A12 | Starcharge | Leak device ID in map API | Device enumeration attack | |
| A13 | Xlvren | Leak device ID in map API | Device enumeration attack | |
| A14 | LVCC | Leak device ID in map API | Device enumeration attack | |
| A15 | Hozonauto | 3 APIs can manipulate other vehicles via VIN | Device manipluation | NVDB-CVAD-2023645555 |
| A16 | DFPV | Steal SMS verification code from login API and login to arbitrary account | Account hijack | NVDB-CVAD-2023839204 |
| A17 | DFPV | 4 vulnerable APIs can manipulate other vehicles via VIN | Device manipluation | NVDB-CVAD-2023287595 |
| A18 | YueHuoCX | One API leaks other user’s access token | Account Hijack | |
| A19 | YueHuoCX | 2 APIs can manipluate other devices | Device manipluation | |
| A20 | YueHuoCX | 3 APIs leak other user’s profile | Privacy leakage | |
| A21 | GXRongYi | 2 APIs leak other users’ profile | Privacy leakage | |
| A22 | GXRongYi | 3 APIs can manipulate other user’s devices | Account Hijack and device manipluation | |
| A23 | YueShiJi | 3 APIs leak other users’ profile | Privacy leakage | |
| A24 | YueShiJi | 3 APIs can manipulate other user’s devices | Account Hijack and device manipluation | |
| A25 | NBLinks | 4 APIs leak other user’s profile | Privacy leakage | CNNVD-2024-54533138 |
| A26 | NBLinks | One API can stop arbitrary device | Device manipluation | CNNVD-2024-54533138 |
| A27 | ZhouDian | One API can get or alter other user’s profile | Privacy leakage | CNNVD-2024-18455990 |
| A28 | Sunmue | Setting uid to 0 can get all users' recent orders | Privacy leakage | |
| A29 | YTD | One API can access merchant's privacy, device ID, status and secret field | Privacy leakage | |
| A30 | BDT | One API can query merchant’s privacy | Privacy leakage | |
| A31 | Lime | One API can simultaneous reserve multiple devices | Device manipulation | |
| A32 | GOON | One API can exploit free test account to abuse devices | Payment bypass | |
| A33 | Helbiz | One API can pause devices after devices are return | Device manipulation | |
| A34 | Helbiz | One API can make one’s e-scooters keep unlock | Use device in free |
Device Vulnerabilites
| ID | Device | Vulnerability Details | Impact | ID |
|---|---|---|---|---|
| D1 | Teld | Use a common key for encryption and authentication | Device impersonate | CVE-2024-32395 |
| D2 | Teld | Device is offline after phantom client re-login | Force other device offline | CVE-2024-32398 |
| D3 | Teld | Order is not correctly reset after re-login | Use device in free | CVE-2024-28306 |
| D4 | Starcharge | Use a common key for encryption and authentication | Device impersonate | CNNVD-2023-13873362 |
| D5 | Starcharge | Device is offline after phantom client re-login | Force other device offline | |
| D6 | Potevio | Use a common key for authentication. No encryption | Device impersonate | CNNVD-2023-45412874 |
| D7 | Potevio | Device is offline after phantom client re-login | Force other device offline | |
| D8 | JieDian | Use common keys for authentications | Device impersonate | CNNVD-2023-64401994 |
| D9 | Xlvren(Charger) | Use a common key for authentication. No encryption | Device impersonate | CNNVD-2023-64401994 |
| D10 | Xlvren(Cabinet) | Use a common key for authentication. No encryption | Device impersonate | |
| D11 | Xlvren(Cabinet) | Device is offline after phantom client re-login | Force other device offline | CNNVD-2023-86646390 |
| D12 | Lvcc(Charger) | Use a common key for authentication. No encryption | Device impersonate | CNNVD-2023-86646390 |
| D13 | Lvcc(Cabinet) | Use a common key for authentication. No encryption | Device impersonate | |
| D14 | Lvcc(Socket) | Use a common key for authentication. No encryption | Device impersonate | |
| D15 | QiXin | No encryption and authentication | Device impersonate | CNNVD-2023-88980307 |
| D16 | QiXin | Device is offline after phantom client re-login | Use device in free | CNNVD-2023-88980307 |
| D17 | QiXin | Order is not correctly reset after re-login | Use device in free | CNNVD-2023-88980307 |
| D18 | MeiTuan | Server terminates the order when devices go offline | Use device in free | CNNVD-2023-18966113 |
| D19 | AnKong | No encryption and authentication | Device impersonate | |
| D20 | AnKong | MQTT message injection | Use device in free | |
| D21 | WZ-Cloud | No encryption and authentication | Device impersonate | |
| D22 | AnSheng | No encryption and authentication | Device impersonate | |
| D23 | BDT | No encryption and authentication | Device impersonate |
Remote Vulnerabilities
| Product | Vulnerability Details | Impact | ID |
|---|---|---|---|
| LuLuChong | 5 APIs leak user’s profile and order infomation. | Privacy leakage | CVE-2024-32395 |
| The device stop API does not verify user access. | Device manipulation | ||
| QSXM | Forge payment argument to alter price | Use device in free | CNNVD-2023-76976427 |
| HQJL | Forge payment argument to alter price | Use device in free | CNNVD-2023-24008724 |
| Dadaball | Forge payment argument to alter deposit amount | Use device in free | CNNVD-2023-76957151 |
| QiXin | Forge payment argument to alter price | Use device in free | |
| Leak device ID in map API | Device enumeration attack | ||
| No encryption and authentication | Device impersonate | CNNVD-2023-88980307 | |
| Device is offline after phantom client re-login | Use device in free | CNNVD-2023-88980307 | |
| Order is not correctly reset after re-login | Use device in free | CNNVD-2023-88980307 | |
| Teld | A sensitive setting API does not verify user access | Hijack administrator permission to use device in free | |
| Leak device ID in map API | Device enumeration attack | CVE-2024-28307 | |
| Use a common key for encryption and authentication | Device impersonate | CVE-2024-32395 | |
| Device is offline after phantom client re-login | Force other device offline | CVE-2024-32398 | |
| Order is not correctly reset after re-login | Use device in free | CVE-2024-28306 | |
| Protivo | One API can login to other user's account using the phone number | Account hijack | |
| Use a common key for authentication. No encryption | Device impersonate | CNNVD-2023-45412874 | |
| Device is offline after phantom client re-login | Force other device offline | ||
| StarCharge | Leak device ID in map API | Device enumeration attack | |
| Use a common key for encryption and authentication | Device impersonate | CNNVD-2023-13873362 | |
| Device is offline after phantom client re-login | Force other device offline | ||
| Xlvren | Leak device ID in map API | Device enumeration attack | |
| Use a common key for authentication. No encryption | Device impersonate | CNNVD-2023-64401994 | |
| Device is offline after phantom client re-login | Force other device offline | CNNVD-2023-86646390 | |
| LVCC | Leak device ID in map API | Device enumeration attack | |
| Use a common key for authentication. No encryption | Device impersonate | CNNVD-2023-86646390 | |
| (Cabinet)Use a common key for authentication. No encryption | Device impersonate | ||
| (Socket)Use a common key for authentication. No encryption | Device impersonate | ||
| Hozonauto | 3 APIs can manipulate other vehicles via VIN | Device manipluation | NVDB-CVAD-2023645555 |
| DFPV | Steal SMS verification code from login API and login to arbitrary account | Account hijack | NVDB-CVAD-2023839204 |
| 4 vulnerable APIs can manipulate other vehicles via VIN | Device manipluation | NVDB-CVAD-2023287595 | |
| YueHuoCX | One API leaks other user’s access token | Account Hijack | |
| 2 APIs can manipluate other devices | Device manipluation | ||
| 3 APIs leak other user’s profile | Privacy leakage | ||
| GXRongYi | 2 APIs leak other users’ profile | Privacy leakage | |
| 3 APIs can manipulate other user’s devices | Account Hijack and device manipluation | ||
| YueShiJi | 3 APIs leak other users’ profile | Privacy leakage | |
| 3 APIs can manipulate other user’s devices | Account Hijack and device manipluation | ||
| NBLinks | 4 APIs leak other user’s profile | Privacy leakage | CNNVD-2024-54533138 |
| One API can stop arbitrary device | Device manipluation | CNNVD-2024-54533138 | |
| ZhouDian | One API can get or alter other user’s profile | Privacy leakage | CNNVD-2024-18455990 |
| Sunmue | Setting uid to 0 can get all users' recent orders | Privacy leakage | |
| YTD | One API can access merchant's privacy, device ID, status and secret field | Privacy leakage | |
| BDT | One API can query merchant’s privacy | Privacy leakage | |
| Lime | One API can simultaneous reserve multiple devices | Device manipulation | |
| GOON | One API can exploit free test account to abuse devices | Payment bypass | |
| Helbiz | One API can pause devices after devices are return | Device manipulation | |
| One API can make one’s e-scooters keep unlock | Use device in free | ||
| JieDian | Use common keys for authentications | Device impersonate | CNNVD-2023-64401994 |
| MeiTuan | Server terminates the order when devices go offline | Use device in free | CNNVD-2023-18966113 |
| AnKong | No encryption and authentication | Device impersonate | |
| MQTT message injection | Use device in free | ||
| WZ-Cloud | No encryption and authentication | Device impersonate | |
| AnSheng | No encryption and authentication | Device impersonate | |
| BDT | No encryption and authentication | Device impersonate |